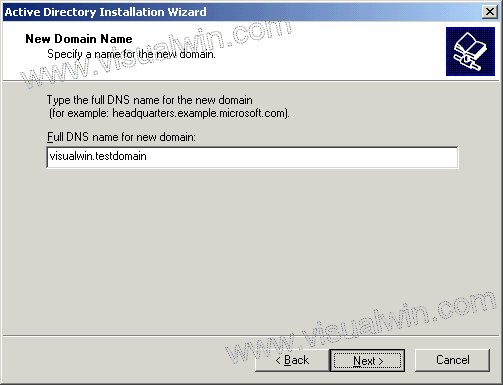
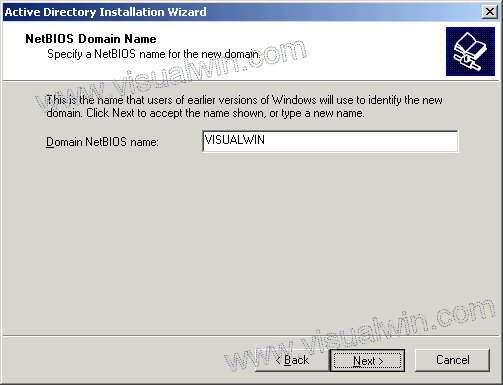
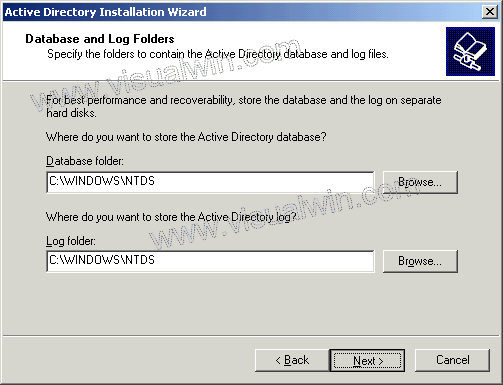
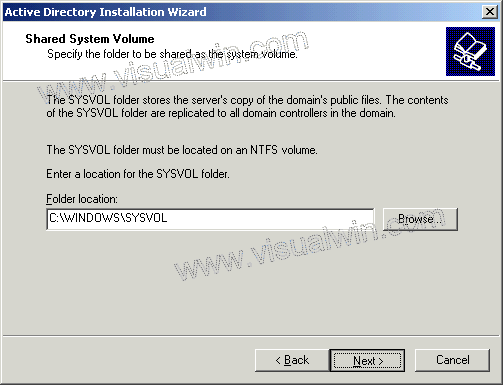
BGP Route Map Examples
The following example shows how you can use route maps to modify incoming data from a neighbor. Any route received from 140.222.1.1 that matches the filter parameters set in autonomous system access list 200 will have its weight set to 200 and its local preference set to 250, and it will be accepted.
router bgp 100
!
neighbor 140.222.1.1 route-map fix-weight in
neighbor 140.222.1.1 remote-as 1
!
route-map fix-weight permit 10
match as-path 200
set local-preference 250
set weight 200
!
ip as-path access-list 200 permit ^690$
ip as-path access-list 200 permit ^1800
In the following example, route map freddy marks all paths originating from autonomous system 690 with a Multi Exit Discriminator (MED) metric attribute of 127. The second permit clause is required so that routes not matching autonomous system path list 1 will still be sent to neighbor 1.1.1.1.
router bgp 100
neighbor 1.1.1.1 route-map freddy out
!
ip as-path access-list 1 permit ^690_
ip as-path access-list 2 permit .*
!
route-map freddy permit 10
match as-path 1
set metric 127
!
route-map freddy permit 20
match as-path 2
The following example shows how you can use route maps to modify incoming data from the IP forwarding table:
router bgp 100
redistribute igrp 109 route-map igrp2bgp
!
route-map igrp2bgp
match ip address 1
set local-preference 25
set metric 127
set weight 30000
set next-hop 192.92.68.24
set origin igp
!
access-list 1 permit 131.108.0.0 0.0.255.255
access-list 1 permit 160.89.0.0 0.0.255.255
access-list 1 permit 198.112.0.0 0.0.127.255
It is proper behavior to not accept any autonomous system path not matching the match clause of the route map. This means that you will not set the metric and the Cisco IOS software will not accept the route. However, you can configure the software to accept autonomous system paths not matched in the match clause of the route map command by using multiple maps of the same name, some without accompanying set commands.
route-map fnord permit 10
match as-path 1
set local-preference 5
!
route-map fnord permit 20
match as-path 2
The following example shows how you can use route maps in a reverse operation to set the route tag (as defined by the BGP/OSPF interaction document, RFC 1403) when exporting routes from BGP into the main IP routing table:
router bgp 100
table-map set_ospf_tag
!
route-map set_ospf_tag
match as-path 1
set automatic-tag
!
ip as-path access-list 1 permit .*
In the following example, the route map called set-as-path is applied to outbound updates to the neighbor 200.69.232.70. The route map will prepend the autonomous system path "100 100" to routes that pass access list 1. The second part of the route map is to permit the advertisement of other routes.
router bgp 100
network 171.60.0.0
network 172.60.0.0
neighbor 200.69.232.70 remote-as 200
neighbor 200.69.232.70 route-map set-as-path out
!
route-map set-as-path 10 permit
match address 1
set as-path prepend 100 100
!
route-map set-as-path 20 permit
match address 2
!
access-list 1 permit 171.60.0.0 0.0.255.255
access-list 1 permit 172.60.0.0 0.0.255.255
!
access-list 2 permit 0.0.0.0 255.255.255.255
Inbound route-maps could do prefix-based matching and set various parameters of the update. Inbound prefix matching is available in addition to as-path and community-list matching. In the following example, the set local preference command sets the local preference of the inbound prefix 140.10.0.0/16 to 120.
!
router bgp 100
network 131.108.0.0
neighbor 131.108.1.1 remote-as 200
neighbor 131.108.1.1 route-map set-local-pref in !
route-map set-local-pref permit 10
match ip address 2
set local preference 120
!
route-map set-local-pref permit 20
!
access-list 2 permit 140.10.0.0 0.0.255.255 access-list 2 deny any
Source link : http://www.cisco.com/en/US/docs/ios/11_3/np1/configuration/guide/1cbgp.html#wp3020